You would have to have been living under a rock to be unaware of the latest news in IT.
Last week, many worldwide systems were victims of the malicious “WannaCrypt” (also known as “WannaCry”) ransomware attack. This attack locks the machine, encrypting all the files and asking for a ransom to be paid.
This has had wide-reaching and devastating consequences. According to Europol, there a have been a reported 200,000 victims of the attack across over 150 countries. This is easily one of the largest scale virus or malware attacks in years, if not ever.
The aforementioned victims have been varied. One of the highest profile casualties has been the NHS in England. This has affected 47 NHS trusts in England and 13 in Scotland, which equates to one in five.
As expected, this has resulted in considerable disruption due to the reliance on the NHS IT systems and patient data. This included several operations being cancelled and appointments and schedules severely affected.
Any disruption certainly was not limited just to the UK as organisations across the globe have been affected. Renault had to “shut down factories across Europe” in the wake to the attack. Hitachi are another who fell victim to the cyberattack, along with US global courier FedEx.
What is ransomware?
Ransomware is a particularly nasty form of virus or malware.
The reason it gets its name is that once infected, all files on the machine in question are locked and held to ransom. A message is displayed on the screen asking for payment – either in real currency or in bitcoin – for the files to be unlocked.
There have been a number of different examples of ransomware, just one example being the Cryptolocker virus.
All of these exhibit the same characteristics, with the virus preventing access to the machine and asking for a ransom to remove it. The message displayed will also issue a countdown timer threatening immediate action or all files will be deleted. This is a legitimate threat and one to be taken seriously.
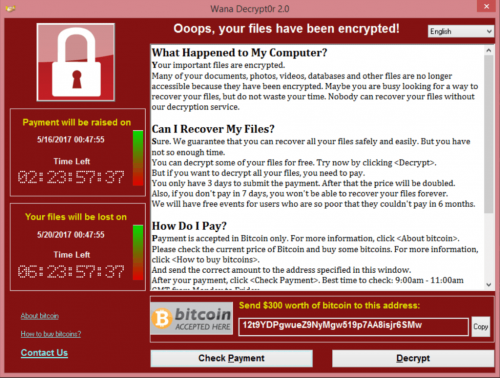
Is it also worth noting that, like any virus infection, this can spread very quickly throughout a network and infect other machines.
The current situation
As it currently stands on Monday 15th, there have been a reported 200,00 victims of the attack across more than 150 countries since Friday when the first reports of the infection started to surface.
There is still a concern that this number will increase with people returning to work and switching on their computers to find they have been infected.
It has been established that a vulnerability in certain versions of Microsoft Windows (Windows XP in particular) has been targeted by this virus. Microsoft have now released a security update to resolve this.
Microsoft have released the following information.
“Seeing businesses and individuals affected by cyberattacks, such as the ones reported today, was painful. Microsoft worked throughout the day to ensure we understood the attack and were taking all possible actions to protect our customers. Additionally, we are taking the highly unusual step of providing a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003. Customers running Windows 10 were not targeted by the attack today.
Details are below.
• In March, we released a security update which addresses the vulnerability that these attacks are exploiting. Those who have Windows Update enabled are protected against attacks on this vulnerability. For those organizations who have not yet applied the security update, we suggest you immediately deploy Microsoft Security Bulletin MS17-010.
• For customers using Windows Defender, we released an update earlier today which detects this threat as Ransom:Win32/WannaCrypt. As an additional “defense-in-depth” measure, keep up-to-date anti-malware software installed on your machines. Customers running anti-malware software from any number of security companies can confirm with their provider, that they are protected.”
The major anti-virus providers such as Webroot, BitDefender and Webroot have issued statements that they provide protection against the virus so if people have updated anti-virus software, they will be protected.
Another recent revelation is that a “kill switch” has been identified in the software, which has effectively halted the spread of the virus. A UK malware expert @malwaretechblog managed to investigate the malware and found that registering a particular domain would initialise the kill switch.
How you can stay protected
We have the following advice to ensure you are protected:
• Always ensure your Antivirus software is up to date – you can usually force a manual update as well, rather than waiting for a scheduled update.
• Always ensure your computer has the latest updates – whether that is Windows Updates, or MacOS updates. Again, if you are unsure when the last updates check/installation was performed, run a manual check.
• Ensure your servers are up to date – for Coretek clients, our ServiceDesk team have been working overtime to make sure this was done over the weekend, and we continue to ensure updates are deployed.
• Ensure any firewalls are switched on and have the latest updates installed.
• Don’t click on any rogue or suspicious links – whether they are on a web page or in an email sent to you. If you are in doubt, DON’T CLICK IT!
• Bonus Tip: Check your backups – hopefully you won’t have to resort to this final step but in the event of an infection, it is likely that you will need to restore from your backups. Don’t wait until getting the infection – check your backups now to make sure these are current. We also recommend carrying out test restores on a regular basis.
If infected, should I pay the ransom?
All advice suggests against paying the ransom. The main reason being that there is no guarantee that the files will actually be decrypted, even after paying the ransom.

Coretek’s position
As yet we have had no reported infections of this ransomware but you cannot be complacent and as such we will be going round each server, client machine and network to ensure the software and firmware patches are to the very latest levels.
We have strong security in place to protect systems for this very reason but we would ask you to please remain vigilant and be aware that most infections will come in through unsolicited email or bundled with downloaded software. If you unsure of anything please log a call with support for further investigation.
Our partners have issued statements relating to WannaCrypt/WannaCry informing that they offer protection against the attack.
SonicWall have released the following information:
“SonicWall Capture Labs identified this attack in mid-April and immediately published protection which was automatically downloaded to all SonicWall firewall customers with active security subscriptions. This occurred well in advance of today’s latest attack.
SonicWall firewall customers with active and properly installed Gateway Anti-virus security subscriptions (either standalone or as a subset of our Comprehensive Gateway Security Suite (CGSS) or Advanced Gateway Security Suite (AGSS)) are safe and are protected from WannaCry ransomware attacks.”
Our recommend Anti-virus solution, Webroot, have confirmed that they provide protection against this attack:
“As a Webroot customer, are you protected? YES. Webroot SecureAnywhere does currently protect you from WannaCry ransomware.”
Future discussions and lessons learned
This situation has brought up a considerable amount of debate and lots of questions have been asked on where blame should be apportioned.
Amid claims that the original tool was developed by the NSA, the chief legal offer of Microsoft stated “we need governments to consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits.”
One positive of this situation is opening up a dialog on the importance of security. The virus targeted older operating systems, such as Windows XP which is now out of support. This shows the importance of keeping IT hardware up to date. It also highlights the importance of keeping Windows and anti-virus software updated.

